
Terrorist attacks on Hospital:
Risk and Emergency Assessment, Tools & Systems
The five steps of the vulnerability approach
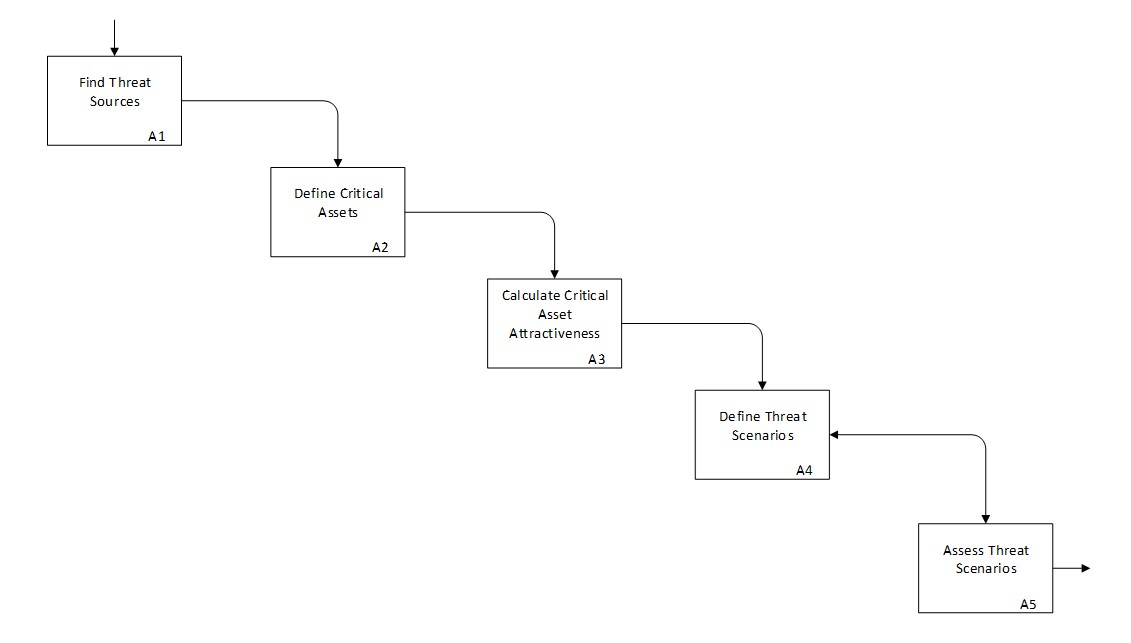
Our vulnerability assessment approach is composed of 5 steps. Steps 1 to 3 enable us to calculate the threat likelihood. Steps 4 to 5 are dedicated to the severity of the hazard.
- Step 1: Assessment of threat sources, by reviewing historical data on terrorist attacks and by analyzing their capabilities and motivations.
- Step 2: Critical assets’ identification, their mapping, their added-value to the hospital, their easiness of access, based on IDEF0 models .
- Step 3: Attractiveness analysis based on pairing of each critical asset and of each threat source to identify potential vulnerabilities per adversary, and to approximate their likelihood.
- Step 4: Define the scenarios and propose the related conceptions. To define the scenarios, we take into account the terrorist profile, type of damage and so on.
- Step 5: Assess the related scenarios. To assess the related scenarios, we take into account the likelihood, the severity and so on.