Terrorist attacks on Hospital:
Risk and Emergency Assessment, Tools & Systems
Step 1: Find threat sources
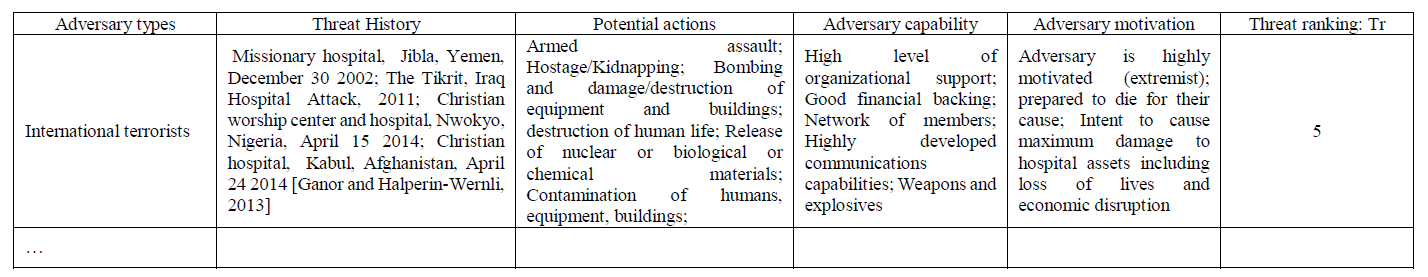
To define the threat sources, we review the historical data on terrorist attacks (including criminality which could act as a henchman), and their dynamics. The attacks can occur in similar contexts (same nation, same sector, same social context…) or can occur in different contexts (country at war or not, private/public sector…).
To evaluate the adversary hazardousness, we propose to use the following criteria: the financial means (F), the knowledge of the system (K), the technology expertise (E), the level of motivation (M)… These criteria will be set from 1 (very low) to 5 (very high). The threat ranking (Tr) will be measured through a weighted sum and be equal to : Tr = a1 * F + a2 * K + a3 * E + a4 * M with a1 + a2 + a3 + a4 = 1. The following table is shown as an example to present per terrorist profile, their threat history (context, i.e. location and date of attacks), their potential actions, their capabilities, their motivations, and the threat ranking. .