
Terrorist attacks on Hospital:
Risk and Emergency Assessment, Tools & Systems
Step 5: Assess threat scenarios
The objective of the risk assessment is to calculate the risk of the different scenarios. The following table is used as an example to show how we assess threat scenarios. The risk assessment approach applied to scenario estimations is based on the one hand on the following criteria (adversary capabilities, adversary motivation, criticality of assets, ease of asset access, human losses, infrastructure damages, operational damages, and symbolic damages) used for estimating the likelihood and severity criteria and on the other hand on the quantitative evaluation tool used (the linear flow model). Each terrorist scenario is fully developed, its likelihood (ease of causing a threat, and adversary motivation) as well as its severity (losses and damages) is estimated systematically and deeply. The combination of likelihood and severity shall provide an index representing the best combination of both criteria.
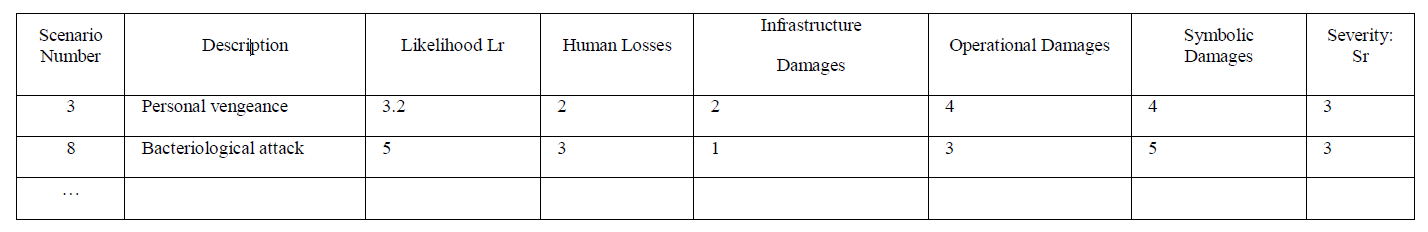
The infrastructure damage index is set to: 1 for a single day disruption for one building, 2 for several days’ disruption for one building, 3 for several days’ disruption for several buildings, 4 for the activity cessation for one building, and 5 for the activity cessation for several buildings.
The Human losses are set to: 1 for 1 killed, 2 for less than 5 killed, 3 between 5 and 15 killed, 4 between 16 and 50 killed, and 5 for more than 50 killed.
The operational damages are set to: 1 for a single service interrupted during one day, 2 for a single service interrupted during several days, 3 for several services interrupted during one day, 4 for several services interrupted during several days, 5 for most services interrupted during several days.
The symbolic damages are based on the reduction of incoming patients after attack. They are set to: 1 for 1% reduction, 2 between 2% and 5% reduction, 3 between 6% and 10% reduction, 4 between 11% and 30% reduction, 5 for more than 30% reduction.
In general the risk model assumed for the matrix in the table above, is the risk of terrorist attack modeled by formula: R = Lr x Sr, where the risk R is the product of the likelihood Lr (i.e., the ease of causing a threat per critical assets, ranking from 1 to 5) and the severity of the hazard Sr (i.e., the impact of the terrorist attack as weighted linear combination of four different severity criteria). In the example presented in the table, each severity criteria is supposed to have the same weight so the severity (last column) is calculated as the average of the 4 previous values.